Telecom Security Scanner
Telecom Security Scanner
The best defence is attack, using the attackers mindset allows us to discover new vulnerabilities, best in a real scenario the mobile core network of mobile operators accross the world. This helps MNO to understand their weaknesses and fix them before threat actors exploit them.


Perfect for:
Attacking all technologies from 2G to 5G
Telecom Security built by a telecom operator for telecom operators
SS7
2G/3G signalling abusing MNOs on interception, location tracking, fraud or bypass
Diameter
4G signalling abusing MNOs on interception, location tracking or bypass
GTP-C
2G to 4G abusing MNOs on Denial of Service, data gathering, exploitation of infrastructure and DNS
5GC
5GC bringing more security but still vulnerable to many threats
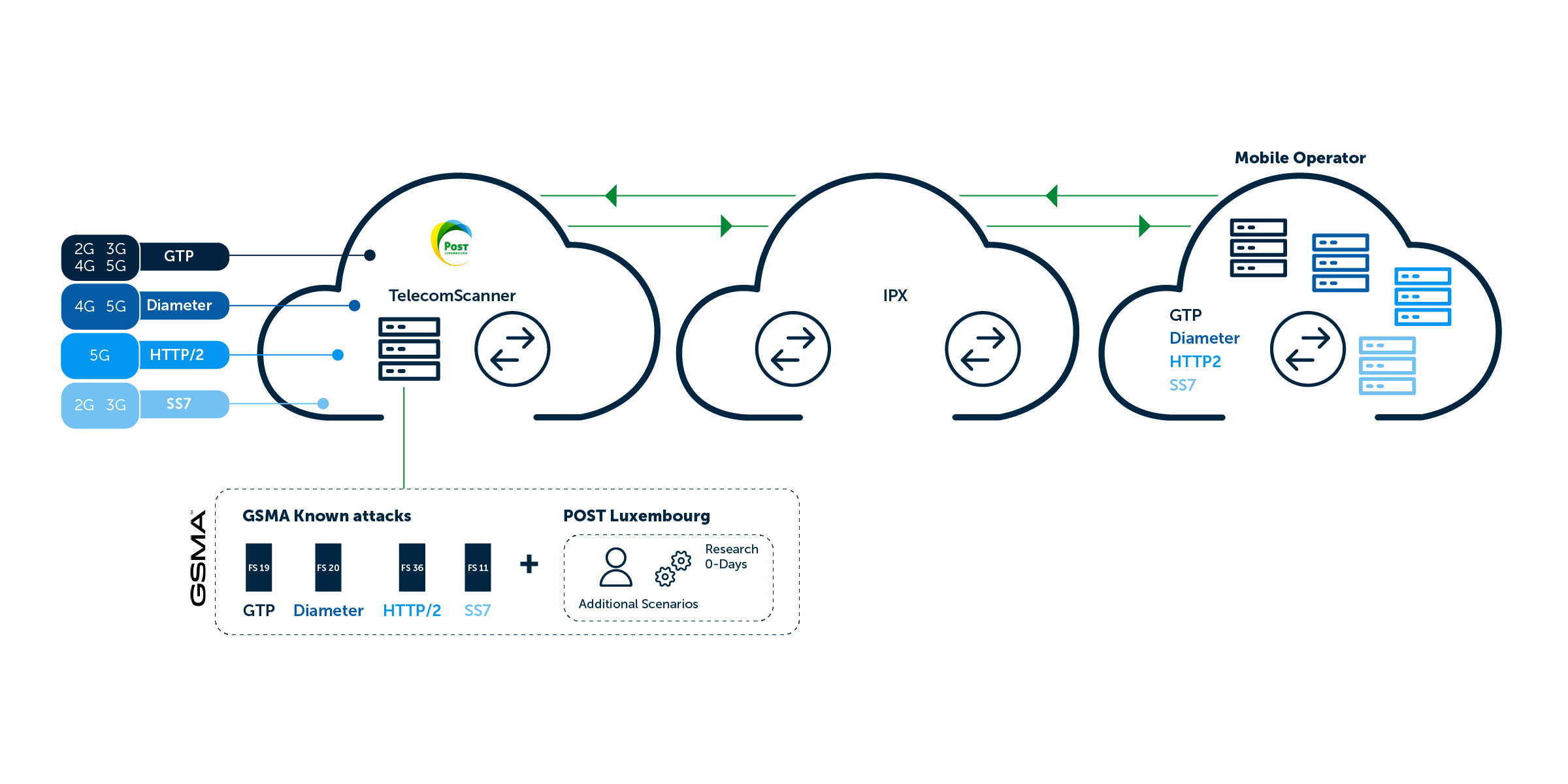
How TSS is setup to attack your network?
All our attacks are launched from Luxembourg from nodes connected to POST Luxembourg production signalling network reaching more than 400+ operators worldwide.








Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
