Cybersecurity weather forecast – 2nd quarter 2020

Each quarter, POST's CyberForce team will describe its perception of the level of cyber threat, based on its security incident management process.
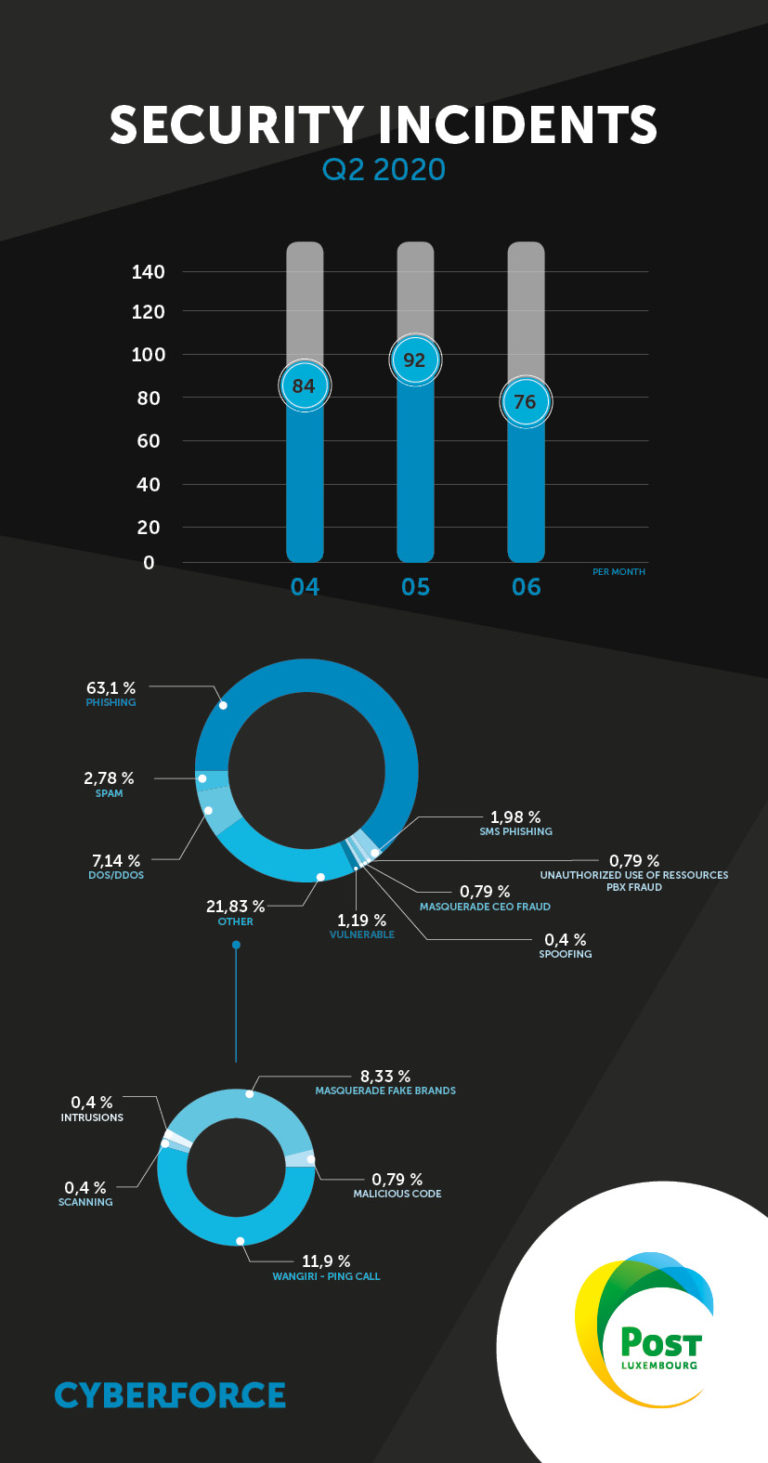
The number of security incidents remained stable in the second quarter of 2020. But although lockdowns are being lifted in Luxembourg and elsewhere in Europe, the number of incidents remains relatively high compared with January and February of the same year.
Fraud – Ransomware – POST Luxembourg
Several companies in Luxembourg have been the target of such attacks. These companies come from a wide range of sectors and include law firms, celebrities, public institutions and large industrial or technological groups. There are no shared characteristics among victims as regards a specific sector or geographical location.
The following ransomware was especially prevalent during the quarter, with some companies charged millions of dollars to recover their data.
- Maze
- Sodinokibi/Sodin/Revil
- Ryuk
- EKANS (Snake)
- CL0p
- Doppel/DoppelPaymer
Ransom leaks: the murky economics of ransomware
This quarter, ransomware has been transformed into a de facto e-commerce business by the following processes:
- Selling ready-to-use ransomware services (ransomware as a service)
- Ransom demands (gathering of company data and execution of ransomware)
- Auctioning data on the black market (ransomware leak)
In other words, an actual economy has developed around this type of incident, led by groups such as REVIL and Maze. We should also note that e-mail ransomware has made a comeback this quarter by targeting individuals. In addition, new ransomware (Avaddon, Philadelphia, Mr. Robot) is emerging and targeting Europe. Businesses and individuals should therefore be cautious about this type of threat.
Wangiri – Ping calls Q2 2020 POST Luxembourg
Instances of “wangiri” fraud (phone calls using foreign premium rate numbers, inducing the victim to call back and be billed for these calls) are still prevalent this quarter. We have confirmed an increase in the volume of phone numbers used to perpetrate such crimes. One call campaign in particular made an impression. On 25 May, a massive call campaign from Fiji was detected. In one day, more than 100 source phone numbers were used to not only victimise a large number of people but also to try to circumvent the protection measures put in place by the operators.
Fortunately, operators have sufficient capacity to detect such incidents using signalling and billing tickets as a source of information. These systems allow automatic blocking rules to be applied to offending numbers to limit the impact on customers.
Fraud – Phishing e-mails
The rate of phishing incidents is particularly high this quarter: it accounts for almost two thirds of security incidents. We counted no fewer than 16 campaigns, the first of which was reported on 18 May with a peak in the last days of May 2020.
Luxembourg remains a prime target for phishing campaigns, but we have noted a shift in focus to customers of Luxembourg banks. We observed four phishing campaigns targeting access to the customer area of Luxembourg banks by stealing the victims' token number.
Since then, new types of phishing have appeared. Token numbers are still the target, but this time the aim is to circumvent 3D Secure protection measures when a customer makes a bank card payment.
Numerous phishing attacks have been reported across Europe. These campaigns were not carried out by e-mail but by defacing a well-known website and redirecting users to a website with a hostname of https://eu.***.xyz
The site in question is a phishing site offering fake competitions to win a phone and asking for the victim's bank details so that a “delivery fee” can be charged for the prize.
These websites do not target one particular operator but several operators in Europe depending on the network used by the potential victim. Thus, when browsing the POST network, a fake POST web page appears. Similarly, when browsing the Telefónica network, a fake Telefónica page appears.
Attacks often occurred over the weekend, catching potential victims unawares.
All these attacks are analysed to identify the resources used by the attackers (web server hosts and e-mail servers of the same scams) and plan a response tailored to the threat.
The CSIRT of POST CyberForce was able to stop various phishing campaigns thanks to:
- Collaboration with hosting companies and the Luxembourg CERTs/CSIRTs community.
- Active “threat hunting” practices, which involve hunting down attacks before they occur in order to avoid recurrences.
SMS phishing
SMS phishing remained stable during the quarter. We have confirmed a trend of using different sender numbers for each recipient. The attackers’ aim is to evade the systems put in place by operators to protect their customers.
One case targeting a Luxembourg bank was reported in which the aim was to steal Token numbers from potential victims.
Masquerade attacks – CEO fraud
CEO fraud increased in the second quarter of 2020.
The targets are always medium-sized and large Luxembourg companies. Attackers prefer to target workplaces where contact with managers is rare. This phenomenon has been accentuated by social distancing measures. Spoofing techniques are becoming increasingly sophisticated: e-mail is still the main means of communication used, but the e-mails are designed in such a way that no one suspects anything.
Fraud – Brand spoofing
The presence of fake company profiles on social media has increased, with a peak at the end of April. Fake Facebook pages impersonating company profiles have been identified, with similar cases in Austria, Switzerland and France. These pages are used to propose malicious content, mainly phishing.
Availability – DDoS attacks
The number of high-impact DDoS attacks has stabilised. Exposed targets have received many recurrent attacks. Other high-profile cases have been reported but in a more isolated and ad hoc manner. We encourage companies experiencing such attacks to contact POST CyberForce to find viable solutions and reduce the risk of recurrence.
Abusive content – Spam
The volume of spam remained relatively stable during the quarter. The COVID-19 crisis has been a source of “inspiration” for some of the people behind this undesirable content, who have put out ads for masks from China or a wide range of accessories to protect against COVID. In addition to e-mail spam, we are seeing a significant increase in SMS spam campaigns, where recipients are encouraged to register with an online gaming site or to contact an e-mail address specified in the SMS.


Written by
PitContact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
Other articles in the category Cybersecurity
DDoS attacks in Luxembourg in 2024
Discover the statistics of DDoS attacks detected in Luxembourg in 2024 by POST Cyberforce.

Author
Paul FelixPublished on
01 February 2024
Preventing DDoS attacks by blocking illegitimate traffic
The number of so-called Denial of Service (DDoS) attacks in Luxembourg is increasing month after month. Cybercriminals are hijacking connected devices to send illegitimate traffic to organisations and saturate connections. These attacks have the effect of degrading the level of service or paralysing the business. To help Luxembourg businesses protect themselves against these attacks, POST has solutions for blocking illegitimate traffic (in real time if needed) before it reaches the organisation's systems.

Author
Paul FelixPublished on
19 December 2023
DDoS attacks in Luxembourg in 2023
Discover the statistics of DDoS attacks detected in Luxembourg in 2023 by POST Cyberforce.

Author
Paul FelixPublished on
15 February 2023


