Cybersecurity weather forecast – 3rd quarter 2020

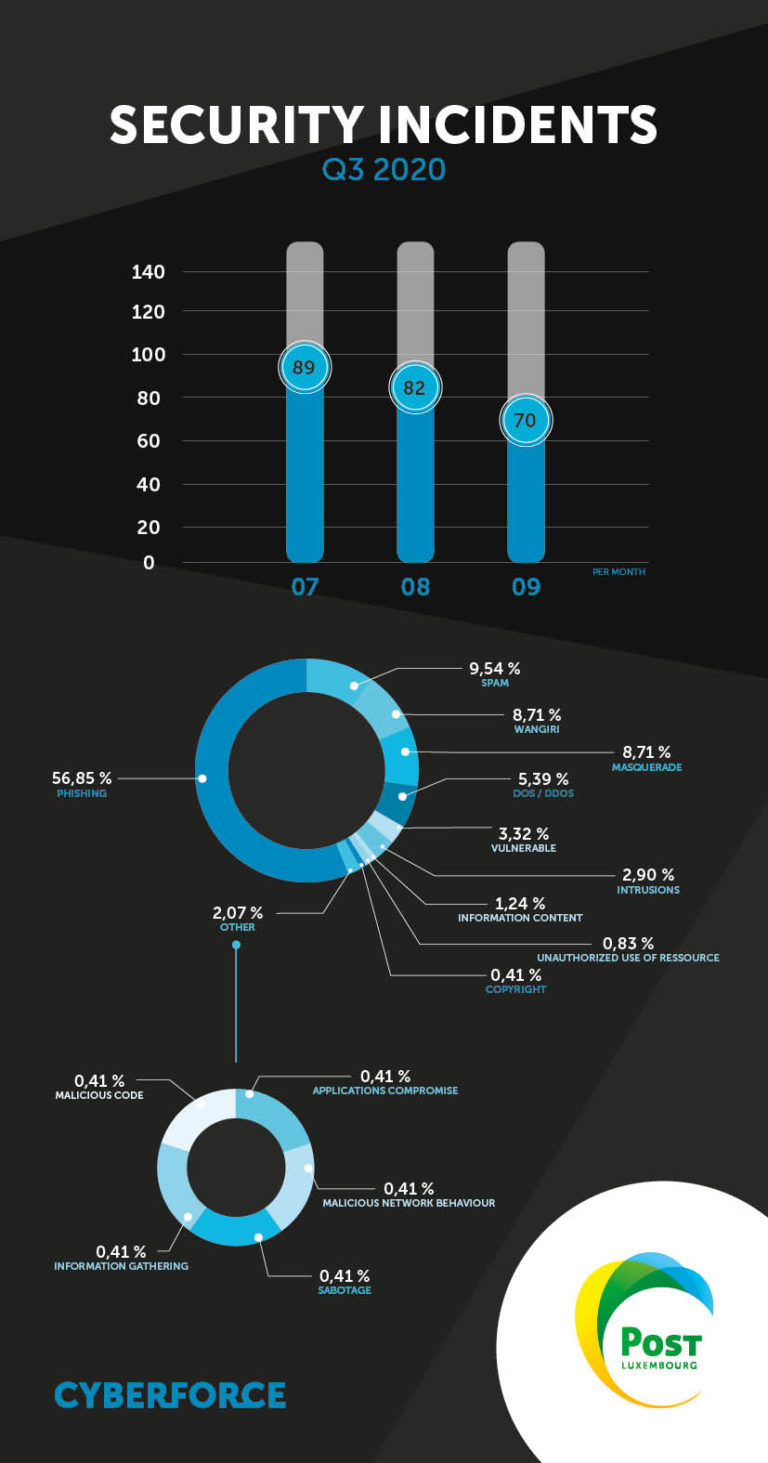
The number of security incidents decreased slightly in Q3.
Although lockdowns were lifted in Luxembourg and elsewhere in Europe over the quarter, the number of incidents remains relatively high compared with January and February of the same year.
Phishing
Phishing campaigns are still the main cause of incidents, despite a slight decrease during the quarter.
Hacking into accounts that use OTP codes for payment or accounts connecting to personal spaces (Webmail, customer accounts, etc.) remain the primary motivation for phishing.
New techniques include the use of public forms and blogs as vehicles for phishing.
Moreover, by systematically redirecting original links, cyber attackers can quickly rotate between several sites to avoid the first URL being blocked, and so bring old campaigns back to life.
Other techniques include filtering by IP address. This allows the phishing content to appear only in the target country and not outside. This technique makes it hard to justify requests to the host to remove the content.
Known techniques are still in play, such as the use of content distributors, adding an extra step for incident response teams trying to determine the source of the host.
We have listed the top 10 hosts (or content providers) used by cyber attackers to perpetrate phishing campaigns:
- Google LLC
- Unified Layer
- Cloudflare Inc.
- Amazon Technologies Inc.
- WebsiteWelcome.com/Hostgator
- DigitalOcean LLC
- InMotion Hosting Inc.
- OVH SAS
- Bitly Inc.
- SingleHop LLC
Finally, we have seen the use of phishing kits featuring logos from source websites, reminding us of the need to protect content on original websites.
The increase in the number of campaigns allows us to more precisely identify the patterns and techniques used in order to improve remediation resources and taken even more preventive measures. In response to the various waves of attacks during the pandemic, the POST CyberForce CSIRT was able to add automated response measures to its anti-phishing arsenal to react even faster and more effectively.
Sabotage
The one recorded case of sabotage had a particularly large impact on an organisation in the country. These incidents serve as a reminder that internal threats to organisations are a reality and should be viewed in the same way as external threats. To respond to this type of incident, organisations must have reliable and unconnected backups, ensure the integrity of the data and, above all, have sufficient response capacity through their own resources or by calling on public and/or private professionals.
DoS/DDoS
New techniques have been noted, one of which is particularly hard to eradicate because of its intermittency. This technique consisted of launching DDoS attacks with intermittent intensity, requiring additional lines of defence to be activated to defeat them.
We also observed the use of compromised objects to perpetrate these attacks.
Victims of such incidents did not have an adequate defence.
Fortunately, there are ways of dealing with these incidents and new techniques. We recommend that targeted organisations protect themselves by taking the necessary steps.
Intrusions
In terms of intrusion, one app was compromised during the quarter, providing us with information on the techniques used and the goals sought. This case involved intrusion via a dictionary attack using a bot.
Our observations suggest that the intention behind these intrusions is to use servers to perpetrate new attacks or to install malicious cryptocurrency mining software (cryptomining). This amounts to using infrastructure for financial gain without the knowledge of its owners.
An SOC makes it possible to guard against this type of attack by detecting intrusions through permanent monitoring of the information system and alerts.
Masquerade attacks – Brand spoofing
There were several waves of brand spoofing during July and September. The aim was to spread fake advertising content on social media for phishing purposes. No new techniques have been detected; the process remains similar to those identified in the past by the POST CyberForce CSIRT. Asking social media platforms to remove content and “Threat Hunting” measures remain effective defences against this type of threat.
Vulnerabilities
Among the most notable vulnerabilities during the quarter, CVE-2020-1350 (source: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1350) and CVE-2020-1472 were particularly critical, with a CVSS score of 10.0 making full control of an organisation's domain possible. Threat Hunting measures confirmed the presence of the vulnerability a few days after publication in Luxembourg. Informing organisations of their vulnerability quickly and proactively, and implementing emergency patches remain the best ways to protect these organisations.
The POST CyberForce CSIRT ensures that the relevant organisations are made aware of such critical vulnerabilities.
Wangiri – Ping calls
A few Wangiri campaigns were observed during the quarter. The techniques remain the same and fraudsters are still using multiple numbers to target more people and thus increase their chances of success.
These techniques are, however, no match for operators’ defence capabilities against this type of incident.
Masquerade attacks – CEO fraud
No instances of CEO fraud were detected in Q3 2020.

Written by
PitContact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
Other articles in the category Cybersecurity
DDoS attacks in Luxembourg in 2023
Discover the statistics of DDoS attacks detected in Luxembourg in 2023 by POST Cyberforce.

Author
Paul FelixPublished on
15 February 2023
DDoS attacks in Luxembourg in 2022
Discover the statistics of DDoS attacks detected in Luxembourg in 2022 by POST Cyberforce.

Author
Paul FelixPublished on
11 October 2022
Cybersecurity: peace of mind with the POST SOC
Using a Security Operations Centre (SOC) allows organisations to constantly monitor activity on their IT systems so as to take quick and effective action in the event of an attack or anomaly.

Author
Alan OlszewskiPublished on
12 July 2022


