Cybersecurity weather forecast – 1st quarter 2020

Each quarter, POST's CyberForce team will describe its perception of the level of cyber threat, based on its security incident management process.
Fraud – Phishing e-mails
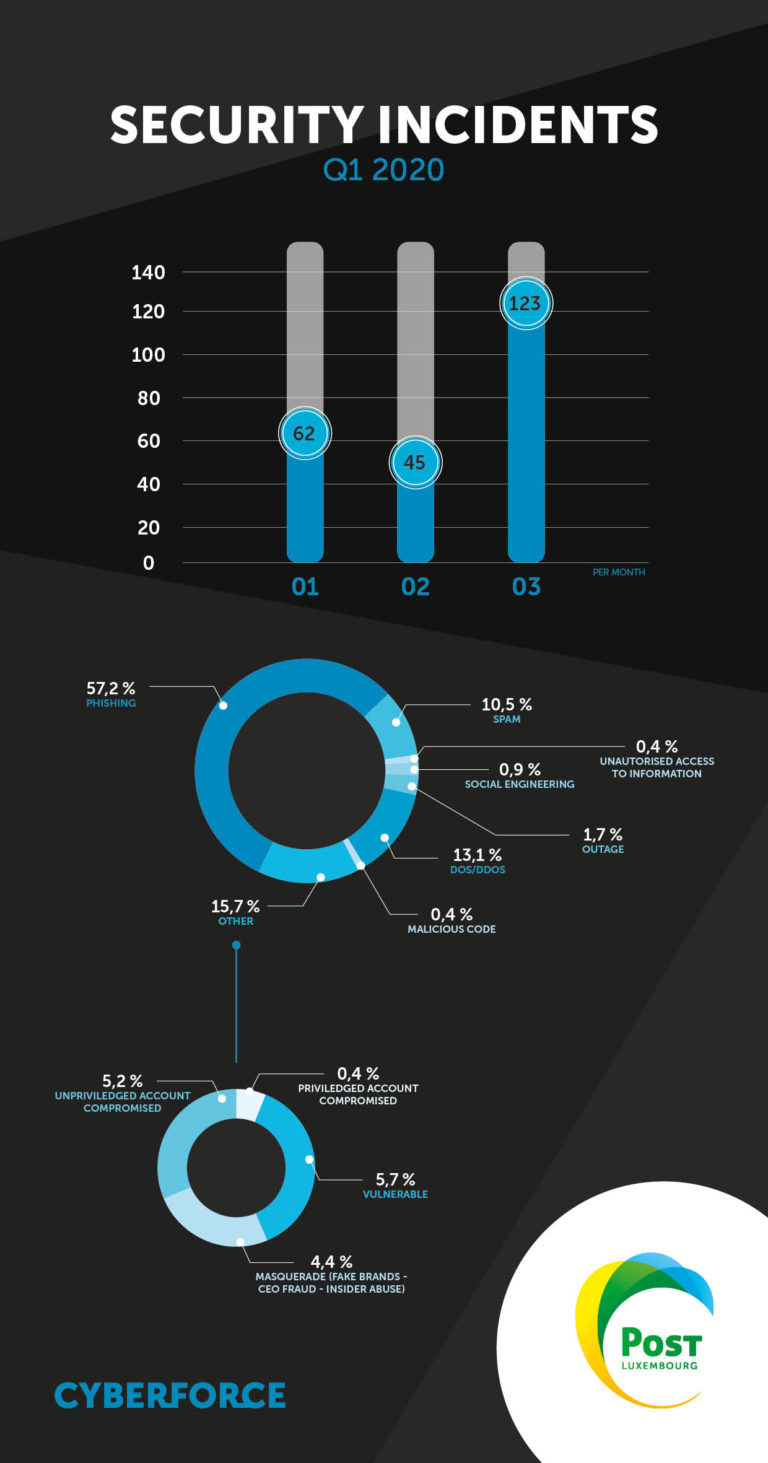
The COVID-19 pandemic and the lockdown measures that followed made cyber attacks particularly prevalent, with a peak in March. The figures show an uptick in the number of phishing attempts in March.
Lockdown has therefore been a boon to cybercriminals, who are taking advantage of the increased public presence in cyberspace to send out more malicious content via phishing.
Phishing took a particularly dark turn during the quarter with multiple campaigns targeting Luxembourg bank customers to steal their login credentials and generate fraudulent transactions without the customer's knowledge.
DDoS
Government lockdown measures have forced companies and their employees to undergo a quasi-mandatory digital transformation to ensure business continuity. This has resulted in a significant increase in the use of networks to enable teleworking. These measures have been illustrated by the presence of DDoS attacks taking advantage of this situation to target organisations.
Fraud – SMS phishing
There has been a noticeable decrease in SMS phishing.
What’s new is that SMS phishing now comes in a different form. There are cases of new techniques using a random sender phone number instead of a unique one as in cases detected previously.
Spam – Wangiri – Ping calls
Wangiri scams are still occurring, despite being quite unobtrusive thanks to measures taken by operators, albeit with relatively little impact. However, the face of the threat is changing as the volume of source phone numbers rises.
Fraud – Ransomware
Recent news shows a resurgence of the ransomware threat to a high level with cases present in Luxembourg. In Europe, large companies and institutions have been a prime target for attackers.
The existence of these cases in Luxembourg shows this to be a threat faced by all companies, irrespective of sector. Any organisation is a potential target.
However, CERT.EU points to an increase in this type of attack against the healthcare sector. This is a particularly sensitive sector in the current pandemic.
Spam – Sextortion
Incidents of “sextortion”, i.e. extortion under threat of disclosure of compromising personal content, have been reported to us. What’s new is that cyber attackers are using new techniques that involve tapping into leaked databases to make a password appear in e-mails. This technique has the effect of making the e-mail appear more credible to the victim so that they fall into the trap.
Fraud – Masquerade attacks – Brand spoofing
Brand spoofing has increased significantly in the last few weeks of the quarter. This scam often entails defacing a legitimate website to sporadically slip in a link to a malicious site offering a fraudulent contest designed to harvest credit card details from potential victims.
What’s new is that cyber attackers are now using social media to commit their misdeeds by posting fraudulent ads.
Fraud – Masquerade attacks – CEO fraud
Instances of CEO fraud have been fairly limited. Cases reported to the POST CyberForce CSIRT demonstrate classic e-mail fraud techniques whereby a cyber attacker impersonates a company director and asks for a large amount of money to be transferred as a matter of urgency.

Written by
PitContact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
Other articles in the category Cybersecurity
DDoS attacks in Luxembourg in 2023
Discover the statistics of DDoS attacks detected in Luxembourg in 2023 by POST Cyberforce.

Author
Paul FelixPublished on
15 February 2023
DDoS attacks in Luxembourg in 2022
Discover the statistics of DDoS attacks detected in Luxembourg in 2022 by POST Cyberforce.

Author
Paul FelixPublished on
11 October 2022
Cybersecurity: peace of mind with the POST SOC
Using a Security Operations Centre (SOC) allows organisations to constantly monitor activity on their IT systems so as to take quick and effective action in the event of an attack or anomaly.

Author
Alan OlszewskiPublished on
12 July 2022


