Cybersecurity weather forecast – 4th quarter 2020

The number of incidents was very high this quarter. In fact, this is the highest level seen since the launch of the Cybersecurity weather forecast in 2020.
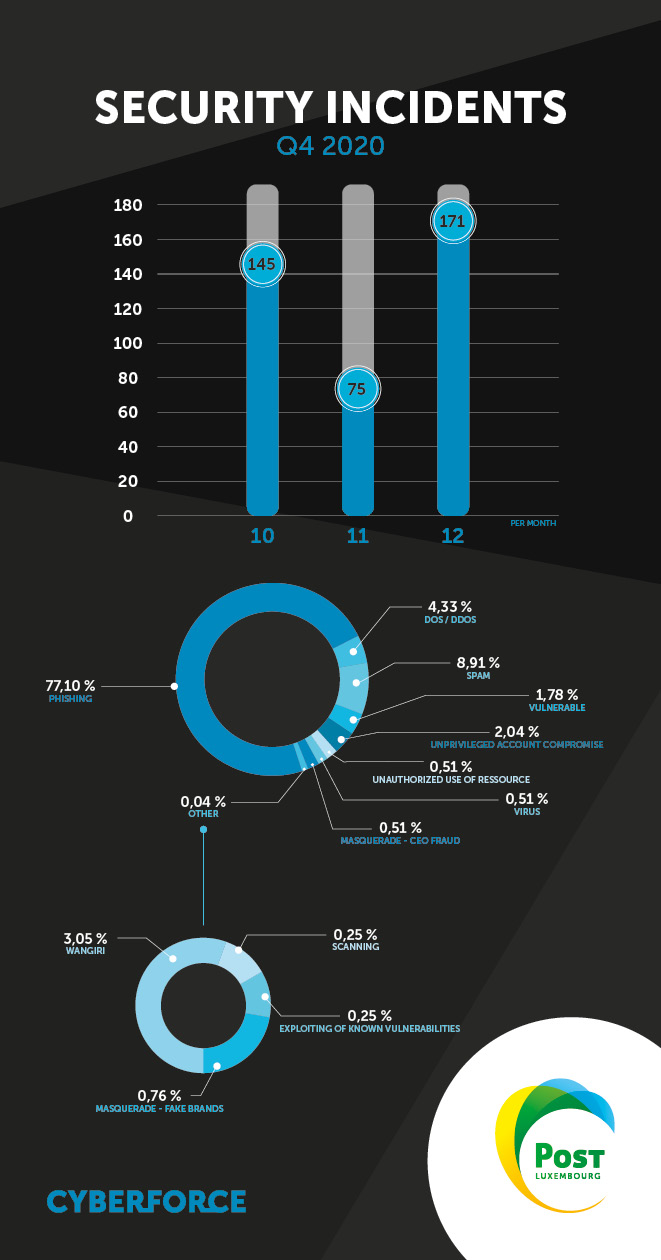
This rise can be attributed to the vast and varied phishing campaigns encountered over the quarter. A link can also be made to the events of the quarter, notably measures relating to the pandemic. This was apparent back in March, when the number of incidents increased significantly.
In terms of impact, we should note that there were vulnerabilities over the period, including with respect to the SolarWinds Orion solution, in the context of new and unprecedented techniques.
We will therefore also present figures giving a breakdown by incident type excluding phishing in order to show where other incidents feature in the cyber threat landscape.
Phishing
Phishing accounted for almost 80% of incidents in the quarter.
POST Luxembourg features prominently among the identities stolen with, for example, requests for bank card numbers following parcel deliveries or requests to change a password before the expiry date.
The aim of such practices is to hack into e-mail accounts in order to access other privileges or bank card numbers for the purpose of committing fraud.
We have also seen a surge in LuxTrust phishing attempts where the aim is to steal the OTP token numbers of potential victims.
In addition to phishing attacks aimed at the general public in Luxembourg, we have also observed highly targeted campaigns aimed at companies. This is known as “spearphishing”. These are campaigns to hack into company accounts in order to prepare for an intrusion into the company's IT system.
Top 10 phishing or phishing redirection hosts identified during the period:
Unified Layer
Google LLC
Cloudflare Inc.
DigitalOcean LLC
WebsiteWelcome.com
InMotion Hosting Inc.
Amazon.com Inc.
A100 ROW GmbH
SoftLayer Technologies Inc.
Amazon Technologies Inc.
The techniques we use to combat these phenomena are evolving. Studying the various phishing kits used by attackers has enabled us to be more proactive in hunting down and stopping attackers perpetrating campaigns. The number of victims is therefore limited and the impact of the campaigns is reduced.
Vulnerabilities
The SolarWinds Orion vulnerability will probably go down as the key development of the period, if not the year, due to the novelty of the techniques used and the fact that it was exploited to attack multiple companies worldwide by the group identified as UNC2452 by FireEye.
In general, exploiting a vulnerability is an inherent part of deploying malware; i.e. it requires an insider within the software publisher.
What was new about the SolarWinds Orion case was the fact that a vulnerability was introduced via the publisher (SolarWinds) and exploited by the group UNC2452.
The group therefore created its own backdoor on updated versions of SolarWinds Orion and infiltrated through updates to the same software. Once the update was complete within the target organisation, the connection to the attacker was established and the attacker could then break into the organisation and carry out an attack on the victim.
Other vulnerabilities have been detected: the exploitation by a group of attackers of a past vulnerability (CVE-2018-13379) on Fortinet SSL VPN where several thousand corporate VPN accounts were exposed on the Internet, putting these organisations at risk of imminent intrusion. A few cases have been reported in Luxembourg.
This type of vulnerability serves as a reminder of the importance of updating to the latest patched versions as soon as a vulnerability is discovered, based on the software publisher’s assurances regarding its development environment’s ability to neutralise cyber threats.
Malicious code
At the end of the year, we saw an increase in the distribution of malicious code. In particular, malicious code known as Emotet, which falls under the Trojan horse category, has been detected in Luxembourg.
Emotet is the most sophisticated virus ever designed. It has infected millions of computers worldwide and opened the door to ransomware attacks.
The malicious code is distributed by e-mail via a password-protected zip file, allowing it to evade antivirus systems. If the victim opens the document, they see a message (Word, Excel) telling them to turn off the protections in place. Once this is done, a script is launched to infect the machine and allow the attacker to take control. Be particularly vigilant when you receive documents from unknown sources or when anything seem suspicious.
DoS/DDoS
A few cases of denial of service attacks have been raised. But DDoS attacks are down compared with last quarter and measures to protect against them are having an effect. It should be noted that attackers tend to target the same victims. This shows that some attackers are determined to do damage to the same victims.
Compromised accounts
We have seen a significant number of accounts being compromised; individual e-mail accounts were the main target. These compromises are the result of successful phishing campaigns. Users must remain vigilant against phishing and never disclose their password or any other confidential information. Leaked login details for an e-mail account are not a trivial matter, especially if this account can be used to access other e-mail or social media accounts, or accounts for other services (bank account, PayPal, etc.).
Wangiri
Some cases of Wangiri fraud were noted at the end of the year, when there were large-scale campaigns. However, no new techniques have been identified and measures to counter these campaigns have proven effective.
Masquerade attacks
The techniques used have changed little from previous instances. The one point to note is that the Luxembourgish language is being used, via translation software, to perpetrate these attacks. This demonstrates a desire for greater targeting and immersion by the attackers.
Unauthorised use of resources
A few instances of IRSF (International Revenue Sharing Fraud) have been observed, and exploitation of vulnerabilities in company telephone exchanges has been detected. This is a first for this type of fraud.
Attackers were particularly active at the end of 2020. Solutions exist to curb this phenomenon. If your company could be the next victim, please contact POST CyberForce CSIRT for more information on these solutions.
Masquerade attacks – Brand spoofing
These instances mainly involved corporate identity theft on social media for the purpose of tricking users in order to perpetrate other attacks (fraud, intrusion or attempted intrusion). This low number confirms that proactive approaches to curbing the phenomenon do help to reduce the number of occurrences.
Spam
We have seen a high volume of spam during the period. The type of spam is still similar (sextortion, winnings of all kinds, inheritance). No new techniques have been observed in this type of incident.

Written by
PitContact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
Other articles in the category Cybersecurity
DDoS attacks in Luxembourg in 2023
Discover the statistics of DDoS attacks detected in Luxembourg in 2023 by POST Cyberforce.

Author
Paul FelixPublished on
15 February 2023
DDoS attacks in Luxembourg in 2022
Discover the statistics of DDoS attacks detected in Luxembourg in 2022 by POST Cyberforce.

Author
Paul FelixPublished on
11 October 2022
Cybersecurity: peace of mind with the POST SOC
Using a Security Operations Centre (SOC) allows organisations to constantly monitor activity on their IT systems so as to take quick and effective action in the event of an attack or anomaly.

Author
Alan OlszewskiPublished on
12 July 2022


