Cybersecurity weather forecast – 2nd quarter 2022

Figures
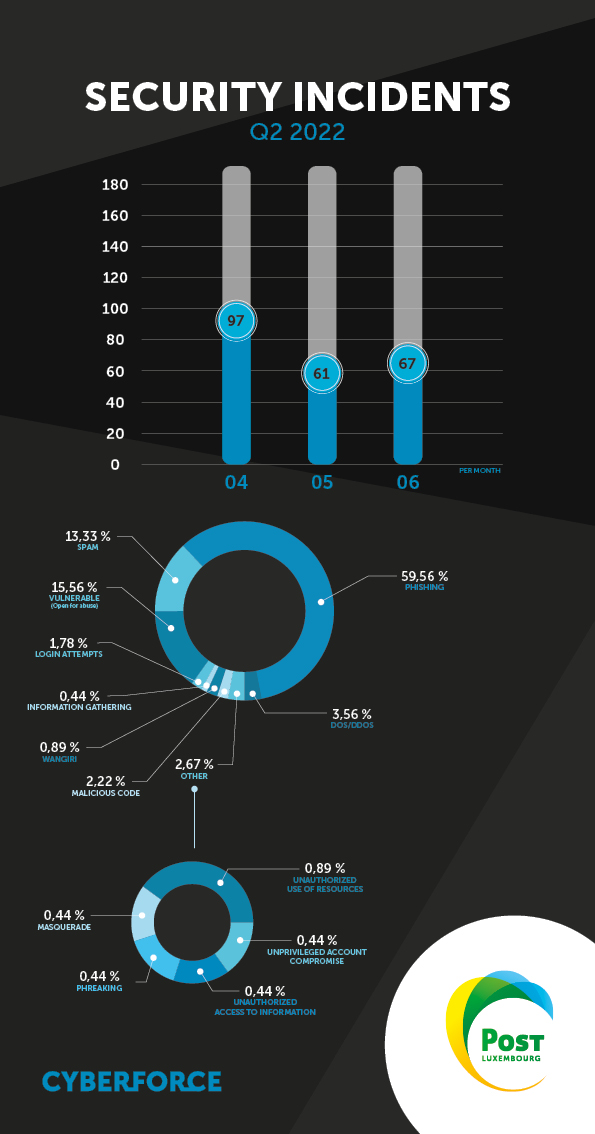
General
We noted a slight decrease of around 10% in the number of incidents from one quarter to the next. The period under review also saw a resurgence of Emotet and Qakbot malware.
Phishing
There were a number of phishing campaigns trying to gather bank card details by pretending to be POST. The pretext is that of the “parcel payment” to steal the victim’s card number, expiry date and security code. This modus operandum accounted for nearly half of the campaigns during the quarter.
Attempts to acquire POST customers’ Luxtrust and webmail details were steady over the quarter. Campaigns targeting Microsoft Office 365 details were down by half on Q1 2022.
A few examples can be found below:
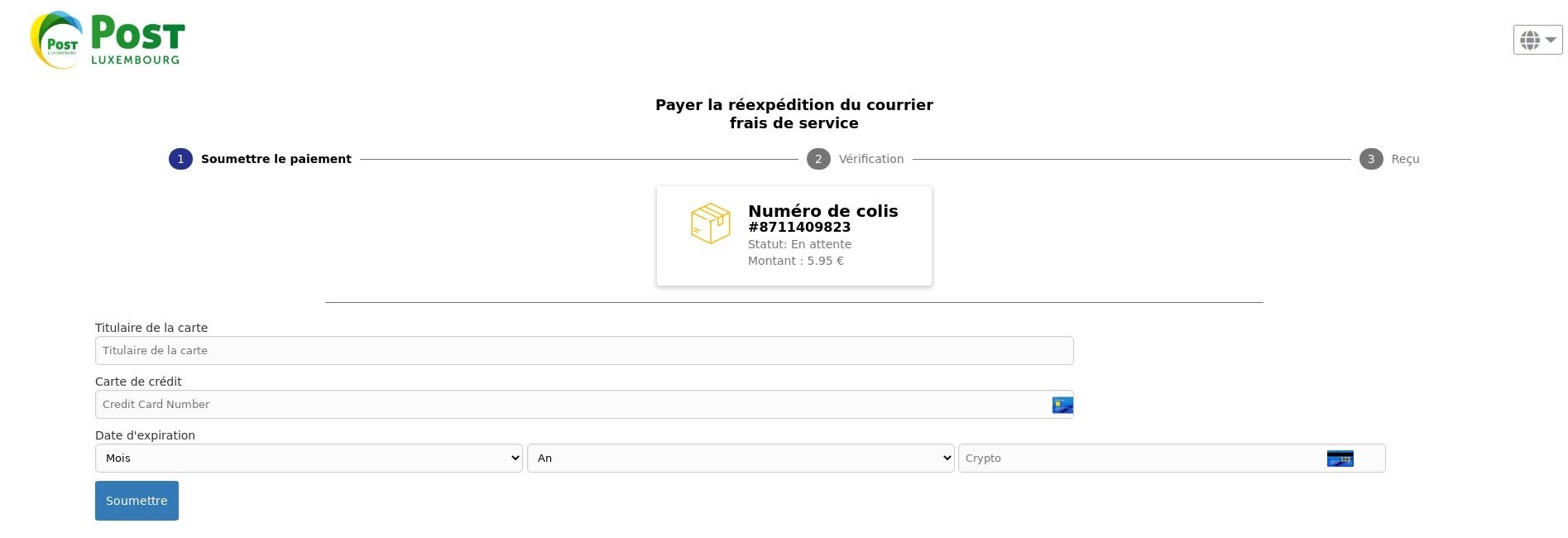
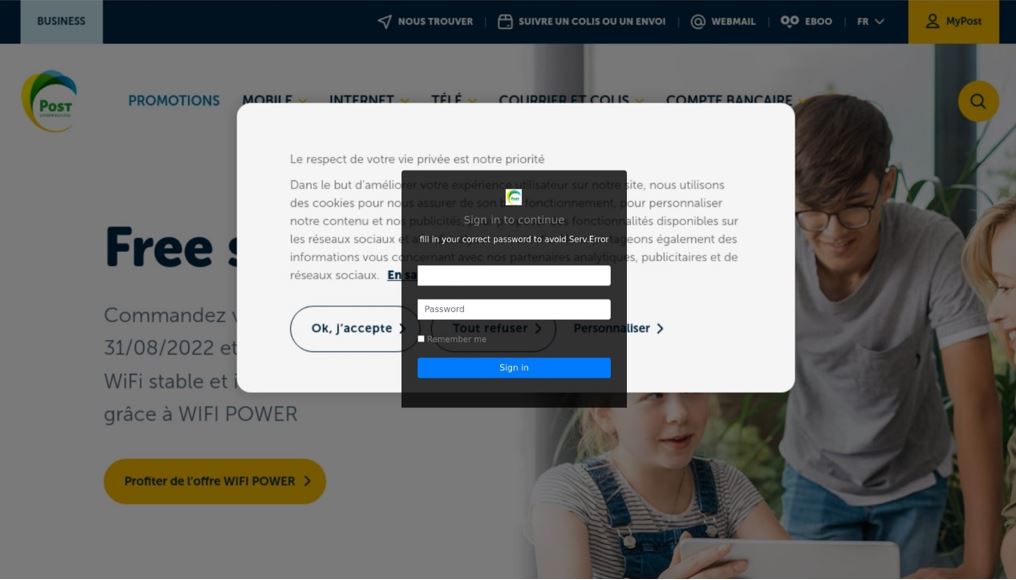
Cybercriminals are using applications to show a screenshot from POST Luxembourg’s official website as wallpaper, making the deception almost perfect. This social engineering technique builds a false sense of trust with victims, making them more inclined to provide their details.
The number of phishing attacks, and their proportion relative to other types of incidents, can be put down to the success in achieving their goal, as well as to the ease of such a attack. The best defence for businesses and individuals against these types of attacks is awareness of the threat, as presented in the cybersecurity weather report.
During the period, we were able to compile the following ranking of hostile actors’ preferred hosting providers for Q2 2022:
- CloudFlare Inc. (=)
- Host Europe GmbH (New)
- Google LLC (-1)
- Microsoft Corporation (-1)
- OVH SAS (+3)
- InMotion Hosting Inc. (New)
- Amazon Data Services India (New)
- Online S.A.S (New)
- Dedibox Customer IP Range (-5)
- Namecheap Inc. (-4)
DoS/DDoS
The number of attacks was fairly stable between the first and second quarters.
In volume terms, the peak was 6.7 Gbps
The most commonly used techniques are:
• TCP connection flood
• UDP Malformed
• ACK Flood, FIN/RST Flood
Malicious code
As described at the start of this report, Emotet and Qakbot malware have been found among the most common attacks.
The default blocking of macros contained in Microsoft Office documents has led cybercriminals to adapt in order to increase their chances of success. This has involved a change of technique to sidestep countermeasures.
The presence of shortcut files (.lnk) as e-mail attachments, containing malicious commands to download and execute dynamic libraries (.dll), lets hackers exploit the victim’s computer. Malicious commands combine lines of classic Windows and Powershell commands. The dynamic libraries downloaded are mutations of Emotet and Qakbot.
To sum up, in cases where the victim clicks on the attached shortcut (.lnk), the scammer gets a foothold in the IT system with a view to achieving their goals (data theft, destruction, ransomware).
We are monitoring these techniques very closely, to see their trend pattern. In the meantime, we encourage you to be careful with this type of threat, which could be dangerous for our information system security.
Vulnerabilities
During the period under review, several systems with exposure to the Internet remained vulnerable to exploitation of Log4shell (CVE-2021-44228) or Microsoft Exchange Server HAFNIUM CVE-2021-26427 (critical).
Although these vulnerabilities were disclosed several months ago, such weaknesses remind us that all patches must be applied to reduce the operating risks to systems before they are exposed to the Internet.
There was the notable presence of a critical vulnerability discovered and actively exploited in the wild, affecting Confluence Server (CVE-2022-26134). This lets an unidentified malicious actor execute arbitrary code remotely. This vulnerability presents a high risk to the securities of organisations, due to its active exploitation in the wild, and the low cost of exploitation for ill-intentioned parties.
Scam calls
A trend has emerged among hostile actors infecting IT systems through telephone servers.
Where telephone login details give access to PBX-type telephone servers on infected machines, cybercriminals can take advantage of this access to make scam calls.
Hence the need to keep your login details safe to ensure the security of each of your information systems. Our CyberForce experts are on hand to help you combat this threat, with advice and solutions.
Durant ce trimestre, nous avons constaté une légère baisse du nombre d’incidents d’environ 10 % par rapport au trimestre précédent. La période a aussi été marquée par une recrudescence des logiciels malveillants Emotet et Qakbot.

Written by
PitContact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
Other articles in the category Cybersecurity
DDoS attacks in Luxembourg in 2023
Discover the statistics of DDoS attacks detected in Luxembourg in 2023 by POST Cyberforce.

Author
Paul FelixPublished on
15 February 2023
DDoS attacks in Luxembourg in 2022
Discover the statistics of DDoS attacks detected in Luxembourg in 2022 by POST Cyberforce.

Author
Paul FelixPublished on
11 October 2022
Cybersecurity: peace of mind with the POST SOC
Using a Security Operations Centre (SOC) allows organisations to constantly monitor activity on their IT systems so as to take quick and effective action in the event of an attack or anomaly.

Author
Alan OlszewskiPublished on
12 July 2022


