Cybersecurity weather forecast – 1st quarter 2021

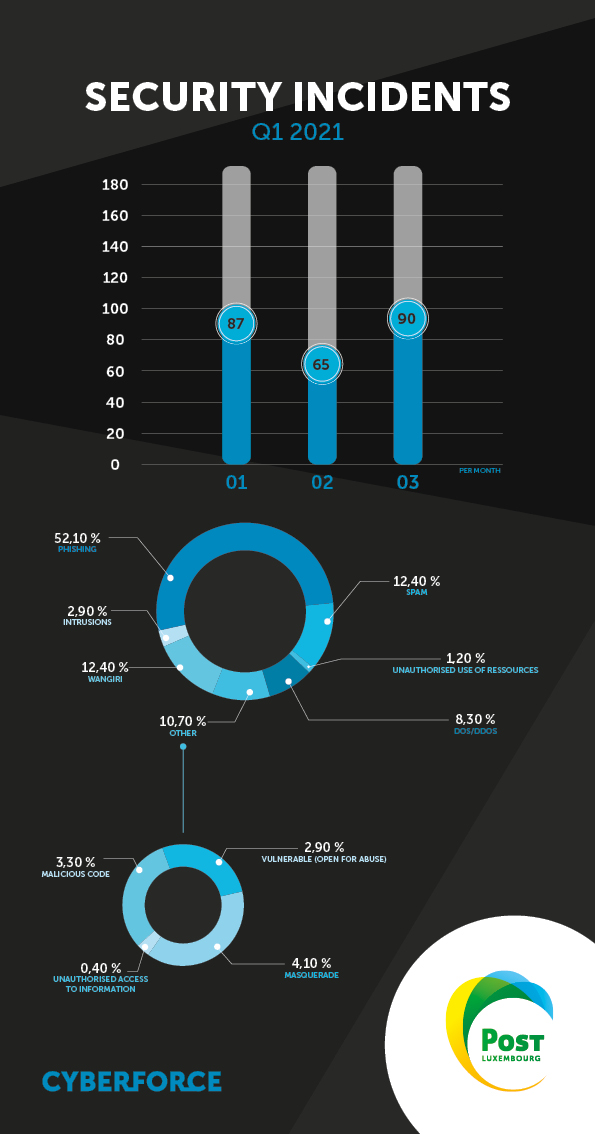
There are very divergent trends to note in this first weather report of the year. Phishing is still the leading cause of security incidents, but the quarter saw vulnerabilities being actively exploited by hacker groups, as well as the emergence of malicious code.
Thanks to Mickaël Le Menach and Eric Chassard from the POST CyberForce CSIRT for editing this weather forecast.
Phishing
We have seen in previous months that phishing campaigns come in spikes. However, there was a downward trend this quarter compared with Q4 2020, both proportionally and in absolute terms.
Some phishing kits used by malicious actors were reused to steal bank card credentials.
The POST CyberForce CSIRT, with help from the Luxembourg CERT community (www.cert.lu), was able to find the victims' card numbers and report them to prevent them being used by malicious actors.
A trend can be observed in phishing scams related to professional cloud services such as Microsoft. The purpose of these phishing scams is to steal users' credentials in order to gain access to target companies’ systems.
Top 10 hosting providers of the quarter:
- Google LLC
- Cloudflare Inc.
- A100 ROW GmbH
- DigitalOcean LLC
- Fastly
- Bitly Inc
- OVH SAS
- Microsoft Corporation
- Eonix Corporation
One new development concerns Facebook: fake profiles and ads are being used to carry out phishing scams on the network. Although Facebook has a moderation policy, we would urge you to be extremely vigilant on social media sites that could host malicious content.
Vulnerabilities
This quarter could be renamed “the quarter of actively exploited critical vulnerabilities”, as the vendors of several exposed applications were affected (including F5 Networks and Pulse Secure). The case of Microsoft Exchange Server is of particular interest. This application was the source of critical vulnerabilities disclosed by Microsoft that could have allowed remote code execution for any exposed application on the internet, enabling the server to be accessed and potentially exploited.
These vulnerabilities were exploited on a massive scale by a group of hackers called HAFNIUM to perpetrate acts of data exfiltration in the context of cyber espionage.
Many false positives have been detected through internet scanning activities to identify vulnerable servers either for possible exploitation or to alert potential victims through scans performed by the CERTs/CSIRT community (cert.lu).
The POST CyberForce CSIRT wishes to reiterate that the threat is real and present in Luxembourg. If you have been affected by these cases, we recommend that you check whether you have the versions with patches against these vulnerabilities.
The POST CyberForce CSIRT is here to help if you encounter an attack or suspected attack on your environment: www.post.lu/csirt
More information is available on the Microsoft Exchange Server vulnerabilities:
- https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-26855
- https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-26857
- https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-26858
- https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-27065
Malicious code
This quarter also saw a larger volume of malicious code compared with previous months. Examples include a variant of the Remcos malware family that was used to gain remote control (Command and Control C2). Despite current techniques for detecting and addressing malicious code in e-mails, via antivirus software that can analyse the behaviour of the malicious code carried, the malicious nature of the latter is particularly difficult to detect. This is because of the techniques used by malicious actors, which include hiding code in encrypted and password-protected zip files that the potential victim is encouraged to open with a password provided in a separate e-mail.
Typically, this code is hidden in Microsoft Office files as an e-mail attachment or via a download link.
Other examples of malware, such as Agent Tesla and Nanocore, have also been observed. The former aims to act as a keylogger; in other words, if you are infected, the aim is to harvest your data via the keyboard and clipboard (copy and paste).
Processes used by this malware:
Agent Tesla
- https://app.any.run/tasks/1e04a5d2-2549-4af1-b03a-d93d0f367b15/
- https://app.any.run/tasks/1675a321-f158-4914-886f-55e6d2c13514/
Remcos
Nanocore
Intrusions
Numerous intrusions have tested our POST CyberForce CSIRT teams. We have observed bots operating in Luxembourg. In other words, malware has been executed from servers to attack other servers. Where this is successful, the malware installs itself and attacks further servers.
This quarter we found a bot exploiting vulnerabilities in unpatched plugins on WordPress-based websites. These events remind us of the importance of applying security patches at all levels, both in the core application and in plugins.
We have also observed intrusions into other applications involving “Credential Stuffing” techniques, where a dictionary of passwords, often obtained through a data leak, is used to gain access. Good password renewal habits for target applications is often all it takes to curb this phenomenon. To keep your access secure, you should also make sure you do not use the same password on every application.
Masquerade attacks
We have identified further attempts at CEO fraud; these still involve the classic strategy of impersonating a company director. Targets tend to be company employees found through professional social networks. From the user’s perspective, it is important not to respond to such requests, whether they come via phone or e-mail. We also recommend that you notify your security provider or the POST CyberForce CSIRT if you subscribe to our CyberSOS services.
We have also seen an increase in Facebook pages impersonating companies. The purpose of these fake pages is to spread phishing scams in order to steal bank card credentials or gather personal data for future attacks. If you see this happening, contact the genuine company immediately to report the fake pages.
DoS/DDoS
The trend in DDoS attacks remains stable, although the threat is still present. In terms of large-scale attacks, we recorded a peak of 16.2 Gbps for volumetric attacks. The techniques used are mainly DNS amplification, UDP flood, ACK flood and QUIC flood. These attacks serve as a reminder of the importance of a rapid response to contain potential damage to your infrastructure. POST Telecom has DDoS mitigation solutions to protect you against these attacks.
Telecom fraud (unauthorised use of resources)
When it comes to fraud involving business telephone equipment (PBX), we have witnessed malicious actors’ determination increasing. They are now attacking configuration vulnerabilities in equipment, whereas perpetrating fraud used to be a matter of finding insecure equipment. As the threat is particularly active, it is important to test the security of your telephony infrastructure to identify potential configuration vulnerabilities.
It is also important to detect and respond to such threats early when the risk arises. Our teams can help you perform these proactive security tests and/or set up detection systems to protect your line against this kind of telephone fraud.

Written by
PitContact us
Do you have any questions about an article? Do you need help solving your IT issues?
Contact an expert







Our experts answer your questions
Do you have any questions about an article? Do you need help solving your IT issues?
